Administrative governance
Overview
Boundary shows which identities access which systems and provides administrative controls to end sessions automatically or manually. Boundary establishes a system of record for your users' access and actions during remote sessions. This capability allows you to maintain security compliance and ensure robust access controls within your environment.
With Boundary, you can:
- Monitor access: Track all systems access, ensuring comprehensive visibility into your users' activities.
- Manage sessions: Automatically exit sessions based on predefined policies or manually end suspicious or unauthorized sessions, providing immediate response capabilities.
- Maintain compliance: Generate audit trails to meet regulatory requirements and security standards.
- Enforce access controls: Implement fine-grained access controls and policies to secure your environment against unauthorized access.
Managing sessions
A session represents a set of connections between a user and a target. A target allows you to define an endpoint with a protocol and default port to establish a session. A session may include a set of credentials which define the permissions granted to the user on the target for the duration of the session.
Session initiation
The session begins when an authorized user requests access to a target. Boundary sets the expiration time and connection limit for the session if you have configured these attributes on the target. The default session duration is 8 hours (28,800 seconds), after which, Boundary closes all associated connections, and the session exits. Boundary retrieves and returns credentials for each associated credential library. Boundary creates sessions in the project scope of the corresponding target. Deleting a project results in the deletion of all of the active sessions in the project.
Monitoring sessions in real-time
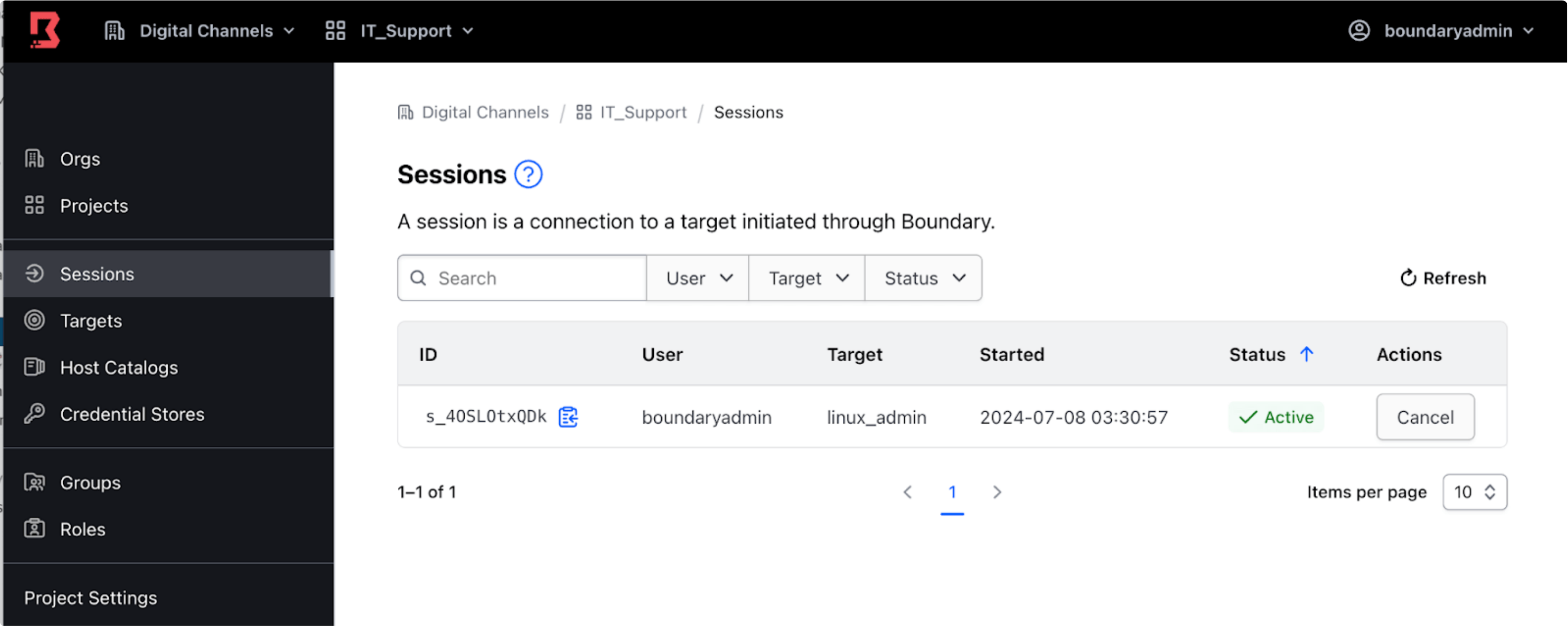
You can view active sessions in real-time, including details like the user's identity, the targets they are accessing, the session start time and the current session status (that is, active, pending, canceling or terminated).
You can use the Boundary command-line tool, desktop app or browser based administrator UI to list all sessions.
For example, run the below command to list all sessions across all your projects using the command-line tool.
boundary sessions list -scope-id global -recursive
To view details of a specific session, use the boundary sessions read command with the session ID.
boundary sessions read -id <session-id>
Similarly, you can use the browser-based administrator UI and navigate to Sessions for a given Boundary organization and project to list all sessions.
Session logging
Boundary logs audit events related to user sessions, such as the creation or cancellation of a session. These logs capture critical details including user's identity, session start and end times, and resources accessed. Audit logs allow you to track user activity and enable security teams to ensure compliance in accordance with regulatory requirements.
HCP Boundary supports near real-time streaming of audit events to supported providers, including Datadog and AWS CloudWatch. This feature ensures that security teams have immediate visibility into user activities and potential security incidents. For self-managed Boundary Enterprise, we recommend streaming audit events to your existing centralized logging solution using log shippers. This approach integrates Boundary's audit logging with the organization's existing monitoring and alerting infrastructure. The example below demonstrates an audit event captured when a user initiates a new session to a remote host:
{
"session_id:s_wYID78DBFL"
"target_id:tssh_N5r14ExLV7"
"scope:id:p_12BUBsbRog"
"scope:type:project"
"scope:name:IT_Support"
"scope:description:IT Support"
"scope:parent_scope_id:o_QljIK3QKUc"
"created_time:seconds:1720352717"
"created_time:nanos:940476000"
"user_id:u_SpwJO5YyPh"
"host_set_id:hsst_I25uYGYFOM"
"host_id:hst_JCTxpHCzQ2"
"type:ssh"
"authorization_token:[REDACTED]"
"endpoint:ssh://10.200.20.213:22"
"endpoint_port:22"
"expiration:seconds:1720381517"
"expiration:nanos:931225000"
}
Please refer to the audit logging section for more details.
Session recording
Boundary also provides auditing capabilities via session recording which is useful for high-security environments where monitoring user actions is critical for regulatory and compliance. Boundary associates a session recording with a target. The session recording captures all interactions that take place during the session, including metadata about the user, target, and any hosts, host sets, host catalogs, or credentials used. A session recording represents a directory structure of files in an external object store that together are the recording of a single session between a user and a target.
Boundary workers record sessions. Workers are the proxy between an end user and a target. A session recording represents connections as separate entities within the recording. Each recorded connection may also contain a recorded channel. This represents a single channel in which the user interacts with the target in protocols that multiplex user interactions over a single connection. For example, the SSH protocol multiplexes user interactions in a single connection, so Boundary records a user's interactions over SSH in a channel.
You can replay recorded sessions through the Boundary administrator UI. This feature allows you to review user actions and investigate incidents, providing context on user actions during that session. Please refer to the find and view recorded sessions for more details. Define session recordings storage lengths based on organizational policies and compliance requirements.
Note: Only the SSH protocol supports session recording.
Session termination
Boundary enables you to manage and exit sessions both automatically and manually. As mentioned, you can view all active sessions in real-time using the command-line tool, Boundary Desktop or browser-based Boundary administrator UI.
Manual termination
You can manually close sessions directly from the Boundary administrator UI with a few clicks or using the command-line tool commands. This capability allows you to close sessions if you detect any suspicious or unauthorized activity.
For example, to close a session, navigate to Sessions for a given Boundary organization and project in the Boundary administrator UI, and click the Cancel button.
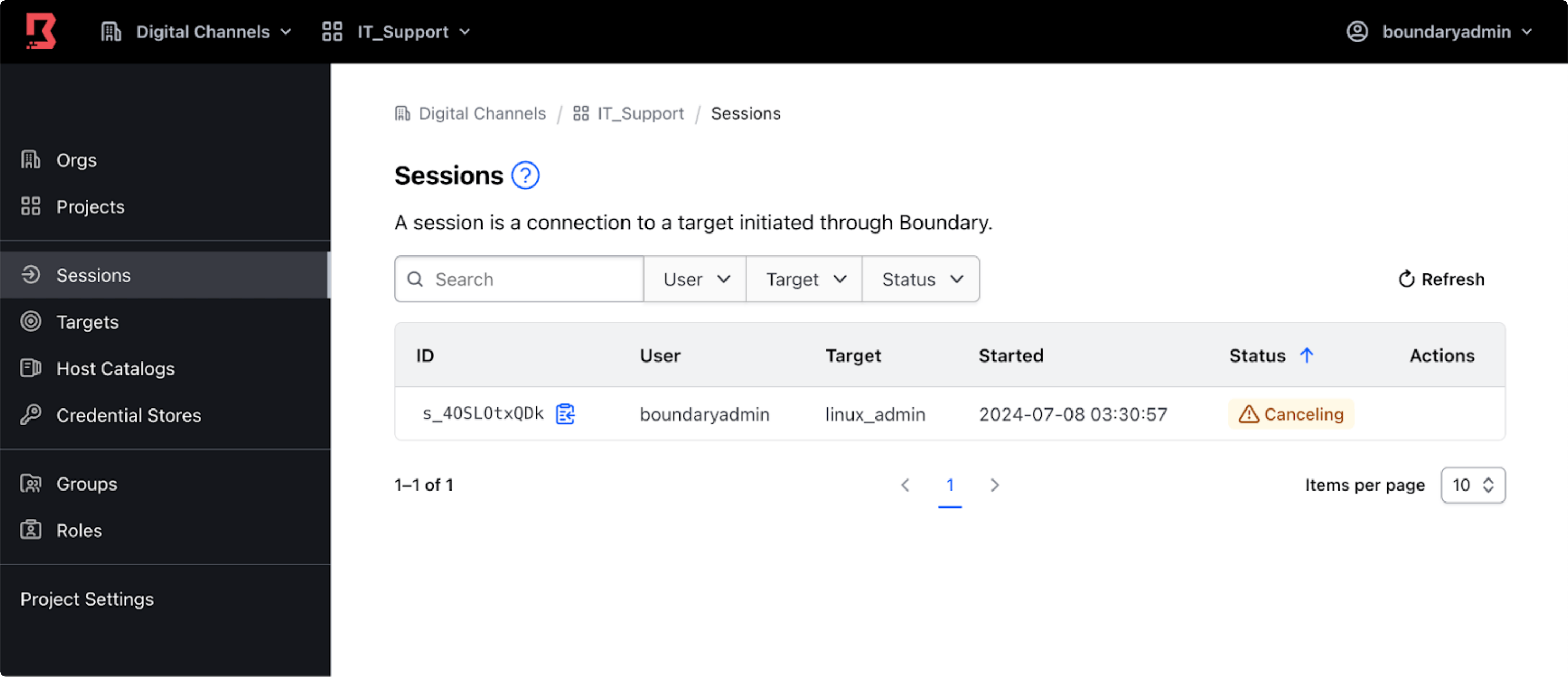
The session status changes to Canceling, followed by Terminated. At this point, Boundary closes the user's connection to the session's associated target.
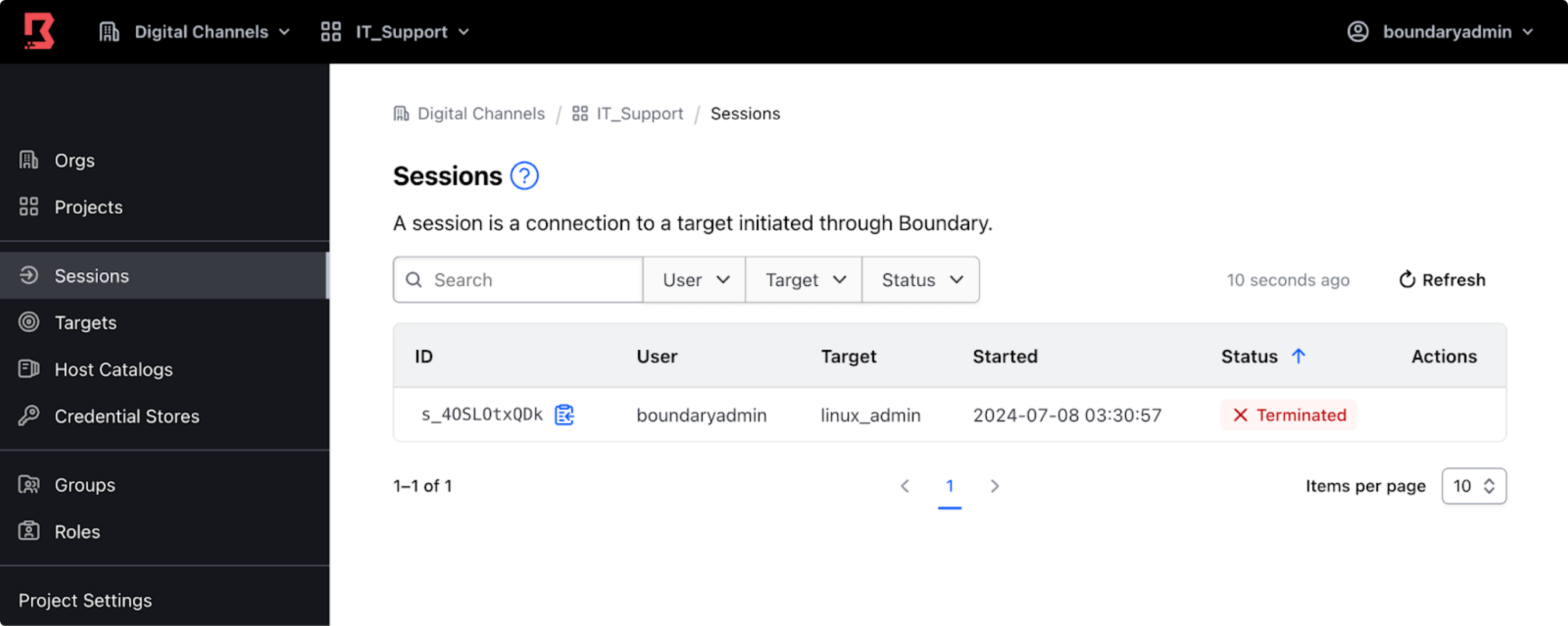
Similarly, to close a specific session using the command-line tool, use the boundary sessions cancel command with the session ID.
boundary sessions cancel -id <session-id>
Automatic termination
You can configure maximum session duration for a target after which the session is automatically terminated. If not configured, Boundary sets the default session duration to 8 hours. This ensures sessions do not remain active indefinitely, reducing the risk of exploitation of unattended sessions. We highly recommend configuring a maximum session duration for a target to limit the time a potentially compromised session remains active, reducing the window for malicious activities. Setting a maximum duration also ensures that unattended sessions are automatically closed, requiring users to re-authenticate to prevent compromise and confirm that access is still valid.